How To Fix Active Directory Replication Even After Tombstone Lifetime Has Expired
In Active Directory Replication between is one of the most impotent element that must happen without any errors, when this procedure stop, the countdown start for default of 60 days which after you get Lingering Objects which prevent the renewal of replication from happening, the stages are :
- Normal Objects – you can manage them from any active directory tools
- Deleted Objects – after delete an object he become tombstone for 60 days, all this changes must be replicate among the DC’s
- Object is removed from Active Directory Database
If the replication is damaged any changes happen in one DC do not replicated to the second DC and so on, causing different object . after 60 days without this sync the DC will refuse to renew the replication until all the problems removed.
First thing to execute is DCDIAG: from the master DC , in order to find who is he , execute in command prompt :
netdom query fsmo
Then run dcdiag
dcdiag /fix
When trying to force replication you can try :
repadmin /syncall /APeD
If the replication is halted for more the 60 days you can try to extend the limit time for Lingering objects by Changing the Tombstone Lifetime Attribute in Active Directory :
The tombstone lifetime is set with the install of the first DCs in a forest for all domains. The tombstone lifetime is not configurable per domain.
| Operating System of the first Domain Controller | Tombstone lifetime (days) |
| Windows Server 2022 | 180 |
| Windows Server 2019 | 180 |
| Windows Server 2016 | 180 |
| Windows Server 2012 | 180 |
| Windows Server 2008 R2 | 180 |
| Windows Server 2008 | 180 |
| Windows Server 2003 R2 SP2 | 180 |
| Windows Server 2003 R2 SP1 | 60 |
| Windows Server 2003 R2 | 60 |
| Windows Server 2003 SP2 | 180 |
| Windows Server 2003 SP1 | 180 |
| Windows Server 2003 RTM | 60 |
| Windows 2000 Server | 60 |
Changing Tombstone Lifetime Attribute
The tombstone lifetime attribute can be modified in three ways: Using ADSIEdit tool, using LDIF file, and through VBScript.in this article we only explain the latest method to change the tombstone time.
USING ADSIEDIT TOOL
To perform this procedure, you will need the ADSI Edit utility. In Windows Server 2008 and above, this component is installed together with the AD DS role, or it can be downloaded and installed along with Remote Server Administration Tools. Refer to Install ADSI Edit for detailed instructions on how to install the ADSI Edit utility.
- On any domain controller in the target domain, navigate to Start ? Windows Administrative Tools (Windows Server 2016) or Administrative Tools (Windows 2012 R2 and below) ? ADSI Edit.
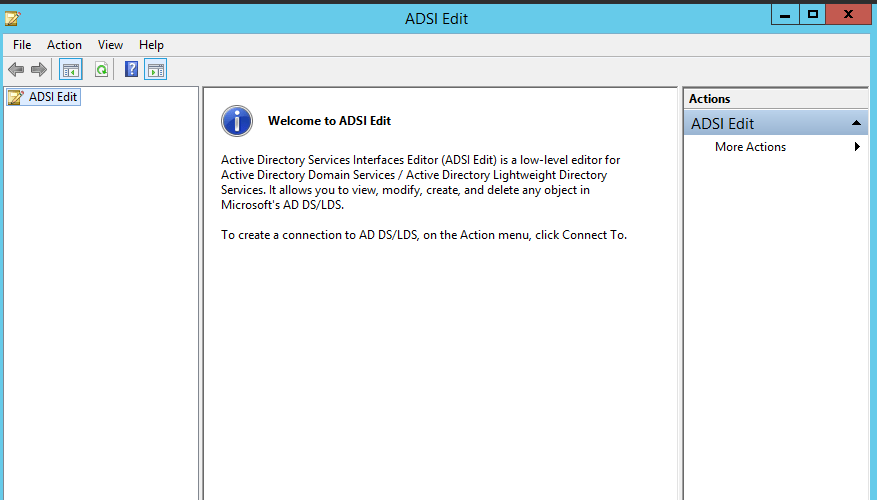
- Right-click the ADSI Edit node and select Connect To. In the Connection Settings dialog, enable Select a well-known Naming Context and select Configuration from the drop-down list.
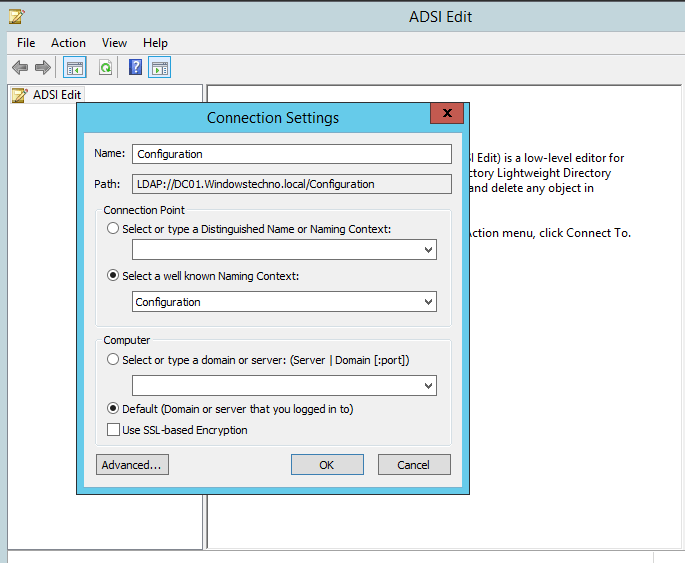
- Navigate to Configuration <Your_Root_Domain_Name ?
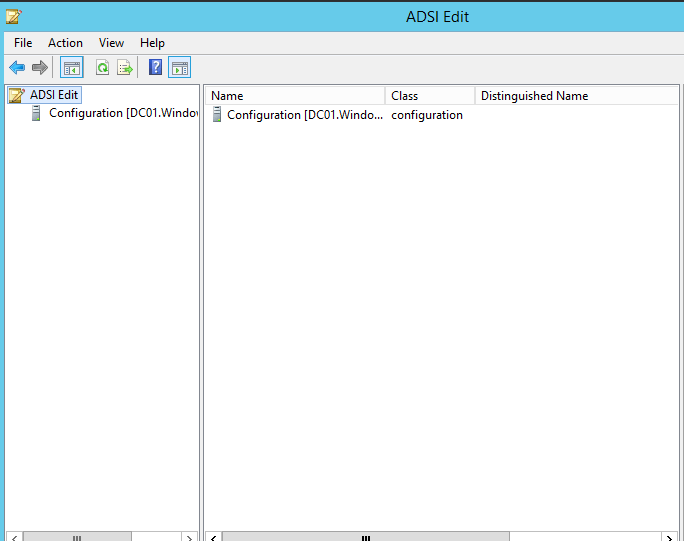
- Expand Configuration CN=Configuration,DC=Windowstechno,DC=Local ?
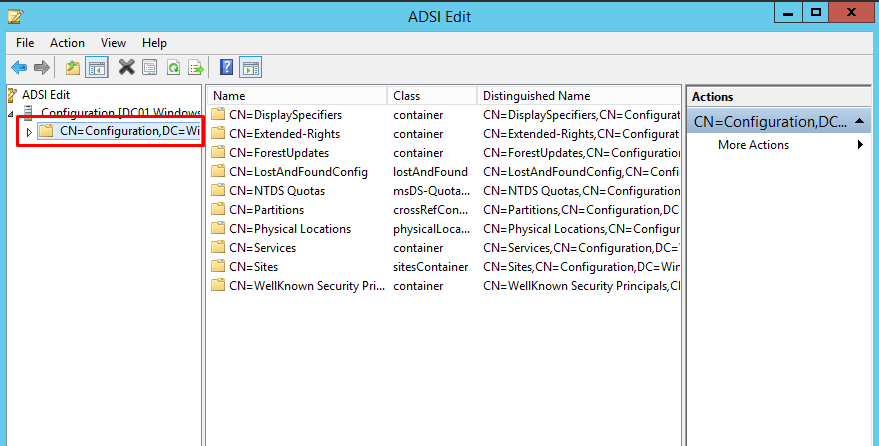
- Expand Services CN=Services ?
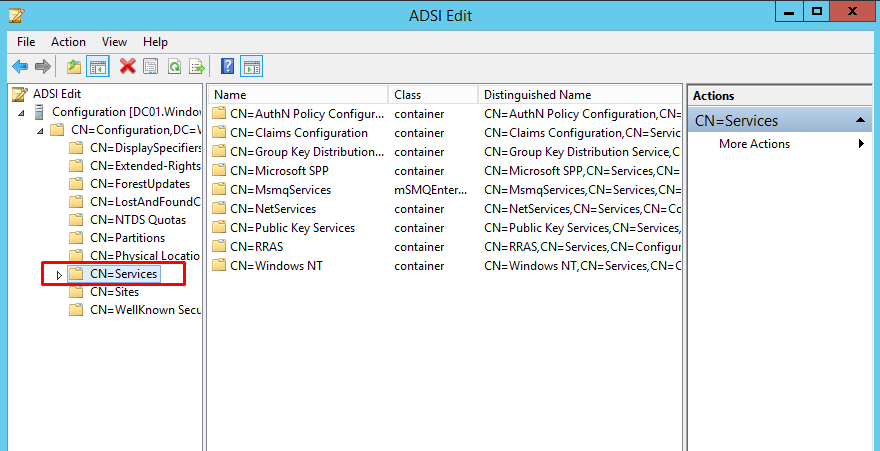
- Expand Windows NT CN=Windows NT ?
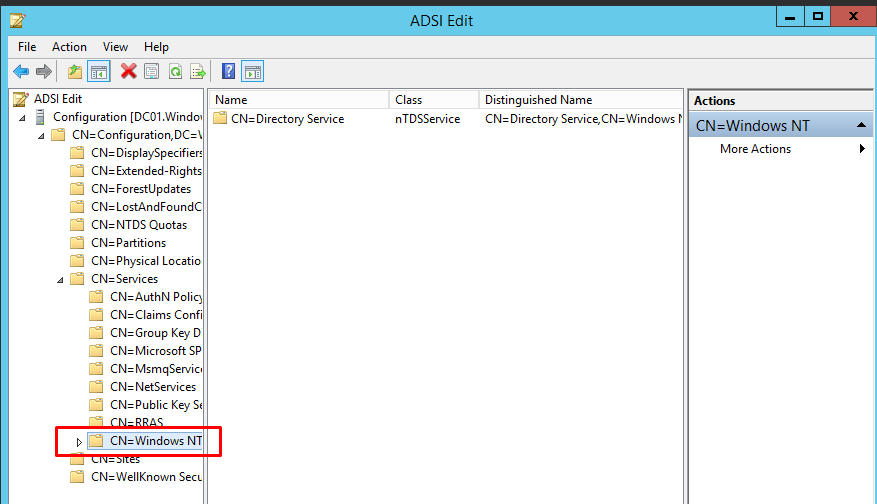
- Expand Directory Service CN=Directory Service.
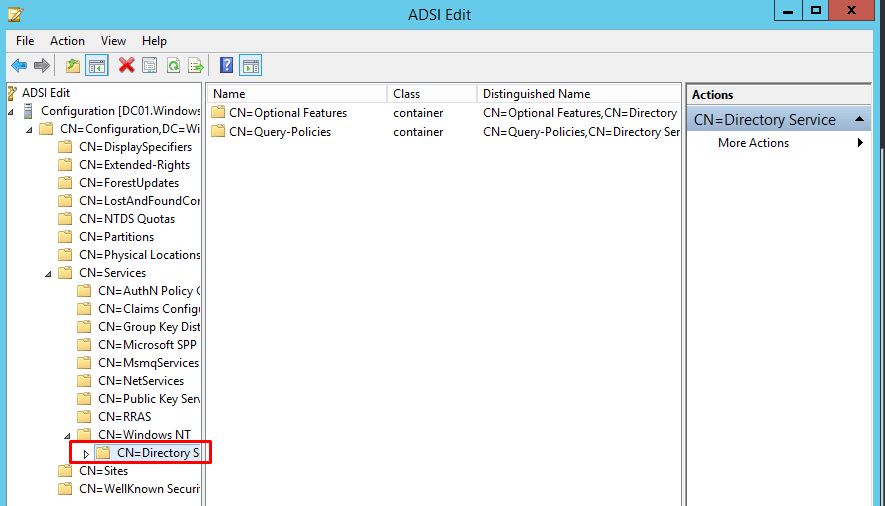
- Right-click it and select Properties from the pop-up menu.
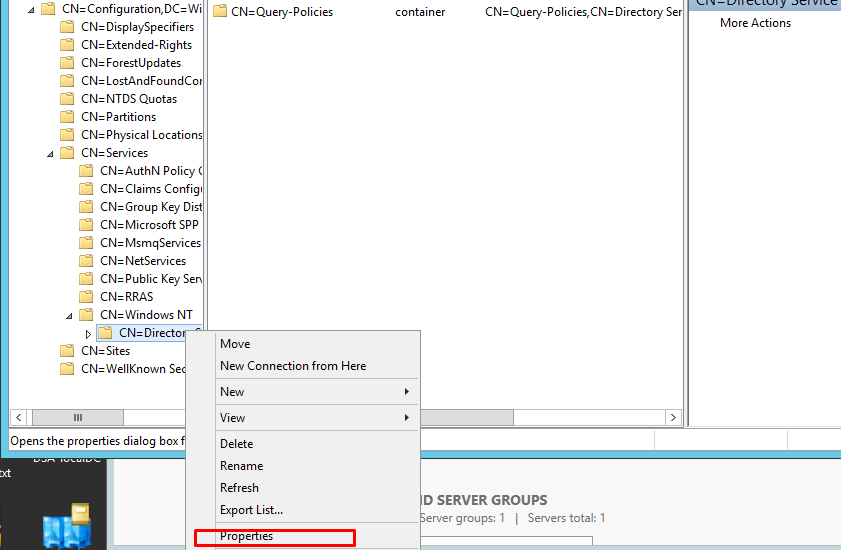
- In the CN=Directory Service Properties dialog, locate the tombstoneLifetime attribute in the Attribute Editor tab.
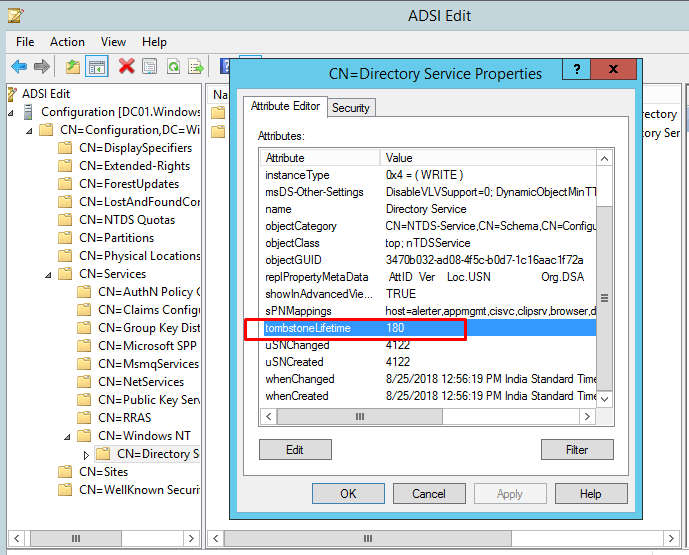
- Edit the tombstone value as per your requirement.
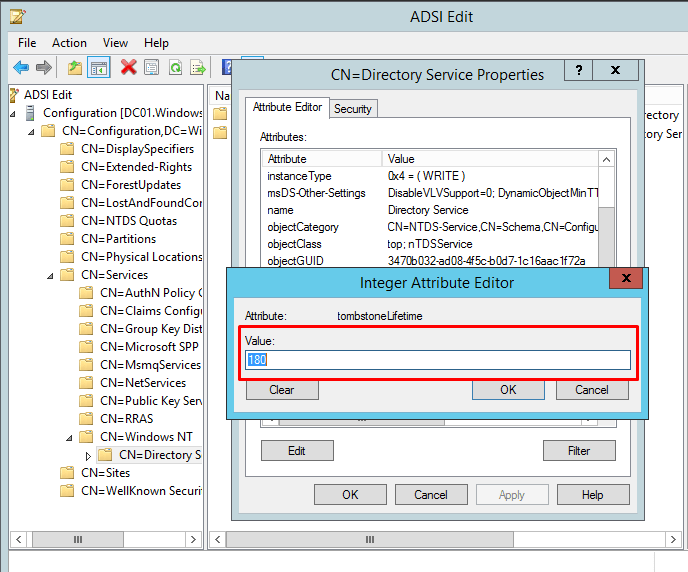
- Click OK.
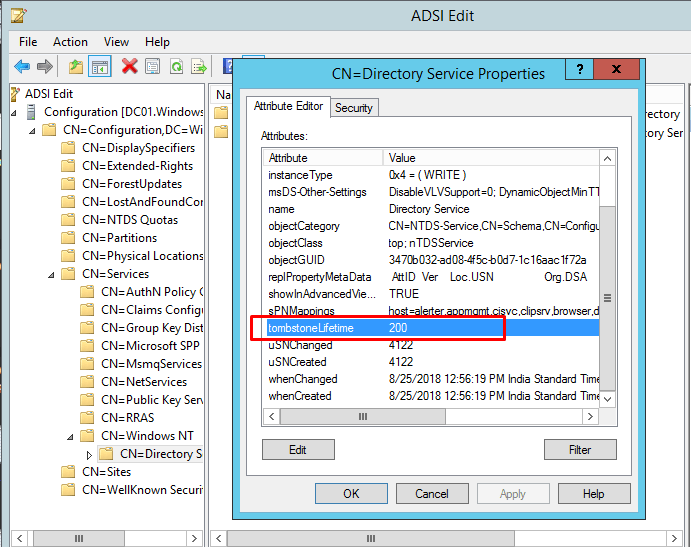
The Tombstone Lifetime has now been successfully changed.
more information about this can be found here : Changing the Tombstone Lifetime Attribute in Active Directory (windowstechno.com)
After this you try force the replication again and show the results and summery of the replication status :
repadmin /syncall /APeD Repadmin /showrepl Repadmin /replsummary
You can also execute from the powershell to get nicer view on the current status :
repadmin /showrepl * /csv | ConvertFrom-CSV | Out-GridView
more information on repadmin example can be found here : Troubleshooting Active Directory Replication – xdot509.blog
How to Troubleshoot Lingering Objects
Lingering Object : An object which has been deleted on a domain controller and even garbage collected but it still remains on another domain controller is termed as a Lingering Object
Preventing Lingering Objects
Of course, it’s most desirable to prevent lingering objects from being created in the first place. There is a registry key called StrictReplicationConsistency — which we’ll refer to as Strict Mode — that will protect a DC from lingering objects:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NTDS\Parameters
ValueName = Strict Replication Consistency
Data Type = Reg_DWORD
Value Data = 1 = Strict 0=Loose
If this value is set to 1, it will prevent a partner from replicating lingering objects to the DC it is defined on. Thus, if every domain controller has Strict Mode enabled, they are protected from lingering objects
How to Find and Remove Lingering Objects in Active Directory
Event ID 1988 proves the presence of Lingering Object in the domain below is the example for the same.
Event Type: Error
Event Source: NTDS Replication
Event Category: Replication
Event ID: 1988
Date: 5/31/2011
Time: 11:58:46 PM
User: NT AUTHORITY\ANONYMOUS LOGON
Computer: EXCHANGE1
Description:
Active Directory Replication encountered the existence of objects in the following partition that have been deleted from the local domain controllers (DCs) Active Directory database. Not all direct or transitive replication partners replicated in the deletion before the tombstone lifetime number of days passed. Objects that have been deleted and garbage collected from an Active Directory partition but still exist in the writable partitions of other DCs in the same domain, or read-only partitions of global catalog servers in other domains in the forest are known as “lingering objects”.
This event is being logged because the source DC contains a lingering object which does not exist on the local DCs Active Directory database. This replication attempt has been blocked.
The best solution to this problem is to identify and remove all lingering objects in the forest.
Source DC (Transport-specific network address):
039c75ff-f65c-4f31-90b4-d68570ff4142._msdcs.rootcon.local
Object:
CN=932c938c-2b18-4704-bb6a-0bbe4ce02dacADEL:781d5c06-bdd9-4423-9772-2f51ef1763cc, CN=Deleted Objects, CN=Configuration, DC=rootcon, DC=local
Object GUID:
781d5c06-bdd9-4423-9772-2f51ef1763cc
User Action:
Remove Lingering Objects:
The action plan to recover from this error can be found at http://support.microsoft.com/?id=314282.
If both the source and destination DCs are Windows Server 2003 DCs, then install the support tools included on the installation CD. To see which objects would be deleted without actually performing the deletion run “repadmin /removelingeringobjects <Source DC> <Destination DC DSA GUID> <NC> /ADVISORY_MODE”. The eventlogs on the source DC will enumerate all lingering objects. To remove lingering objects from a source domain controller run “repadmin /removelingeringobjects <Source DC> <Destination DC DSA GUID> <NC>”.
More information on how to remove lingering objects can be found here : How to find and remove lingering objects in Active Directory | Sandesh Dubey Blog (wordpress.com)
There is a GUI tool to deal with lingering objects called Liquidator v2 :
Introducing Lingering Object Liquidator v2 – TheWindowsUpdate.com
You can download is from here :
Good Luck