How to configure an alert on Active Directory User Locked Out and How To Find what’s locking out an AD account using native auditing
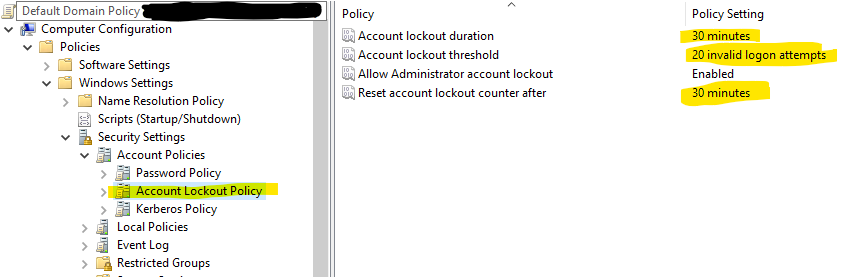
First you need to set the Number of failed login attempt using GPMC (Group policy management ) , The location of the key is :
Computer Configuration -> Windows Settings -> Security Settings -> Account Policies -> Account Lockout Policy
Then you need to to enable user login auditing using the GPMC
Perform the following actions on the domain controller (DC):
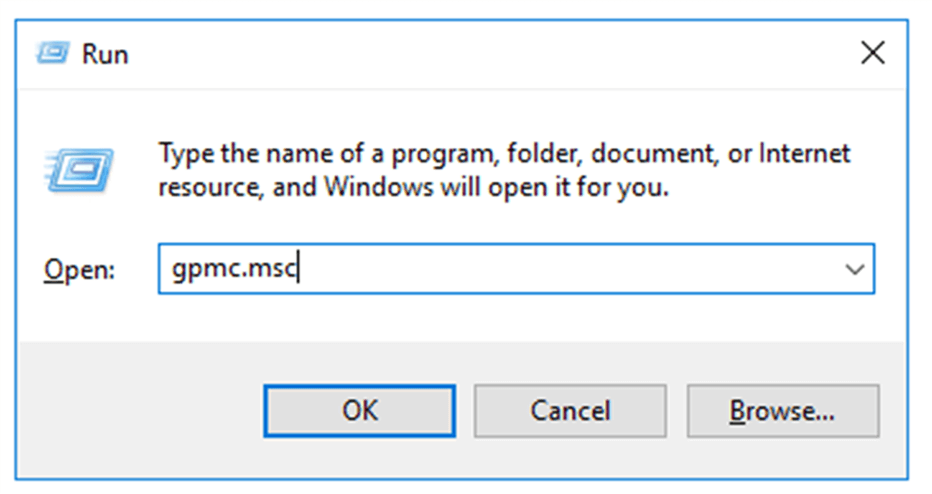
- Open the Start menu. Search for and open the Group Policy Management Console (GPMC). You can also run the command gpmc.msc.
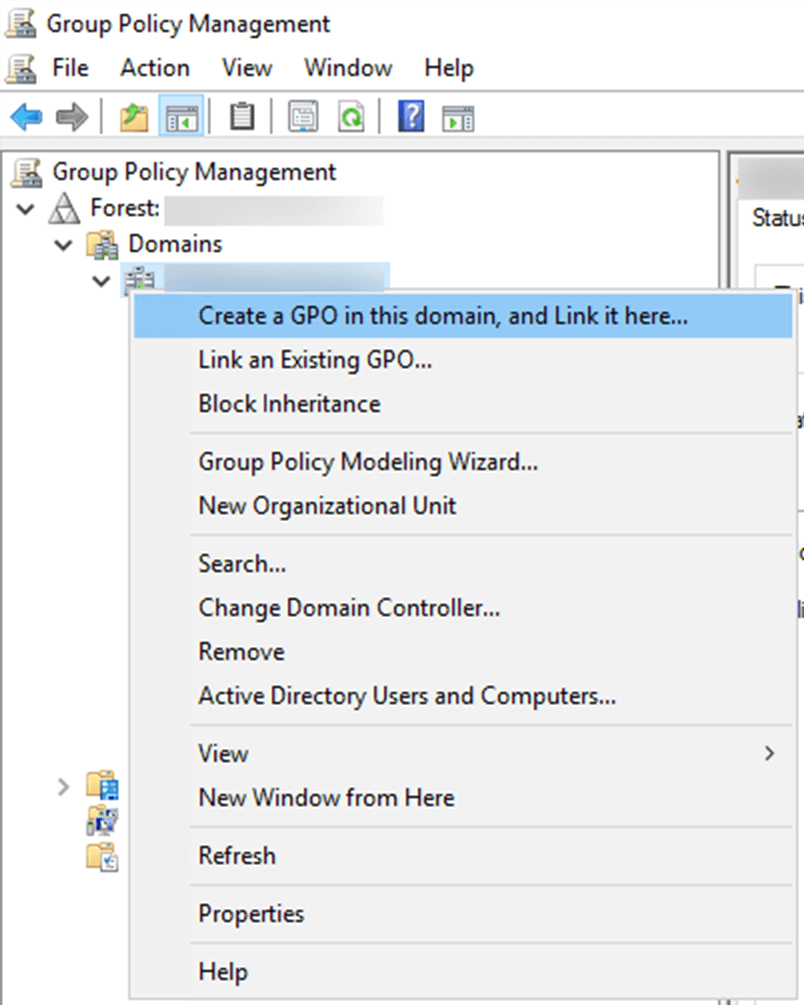
- Right-click the domain or organizational unit (OU) where you want to audit account lockouts, and click Create a GPO in this domain, and Link it here.
Note: If you have already created a GPO, click Link an Existing GPO.
- Name the GPO.
- Right-click the GPO and choose Edit.
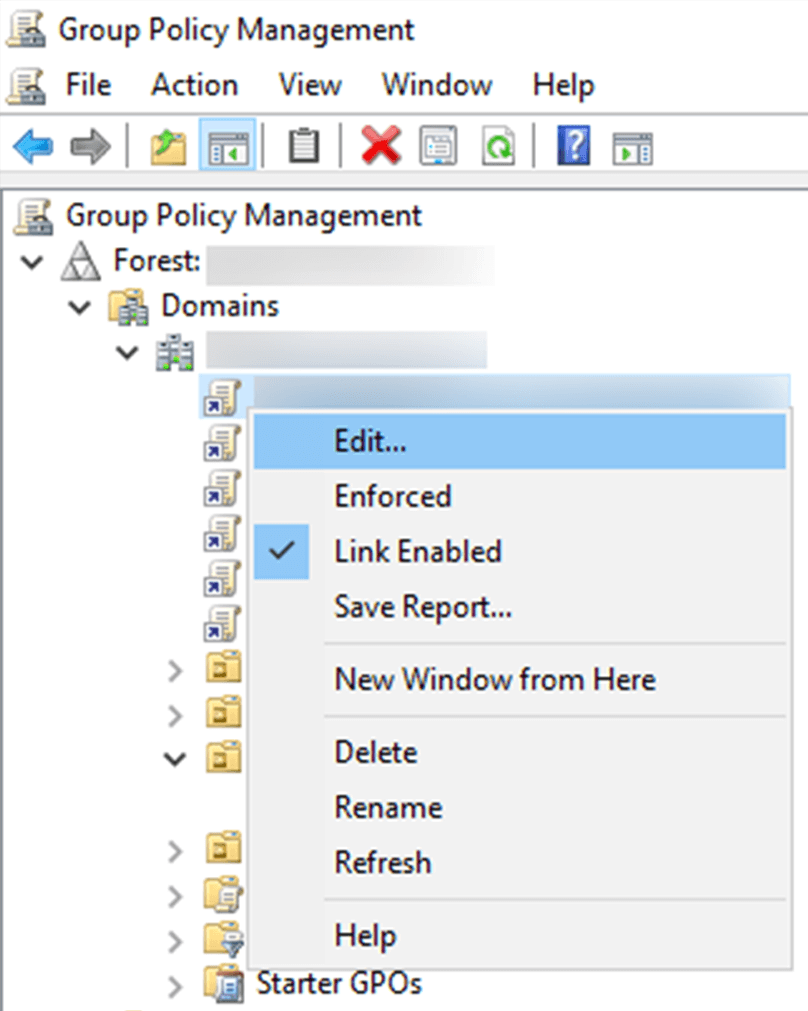
- In the left pane of the Group Policy Management Editor, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Account Management.
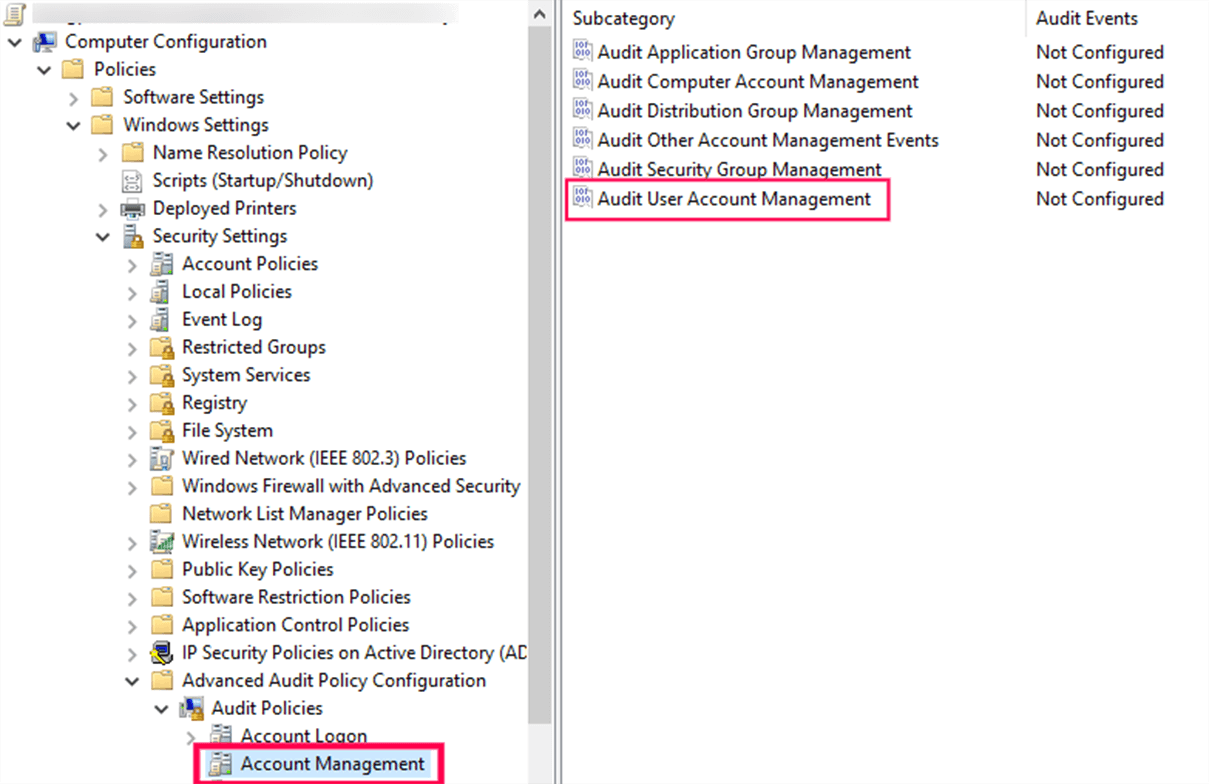
- In the right pane, you will see the list of policies under Account Management. Double-click Audit User Account Management and check the boxes labeled Configure the following audit events, Success, and Failure.
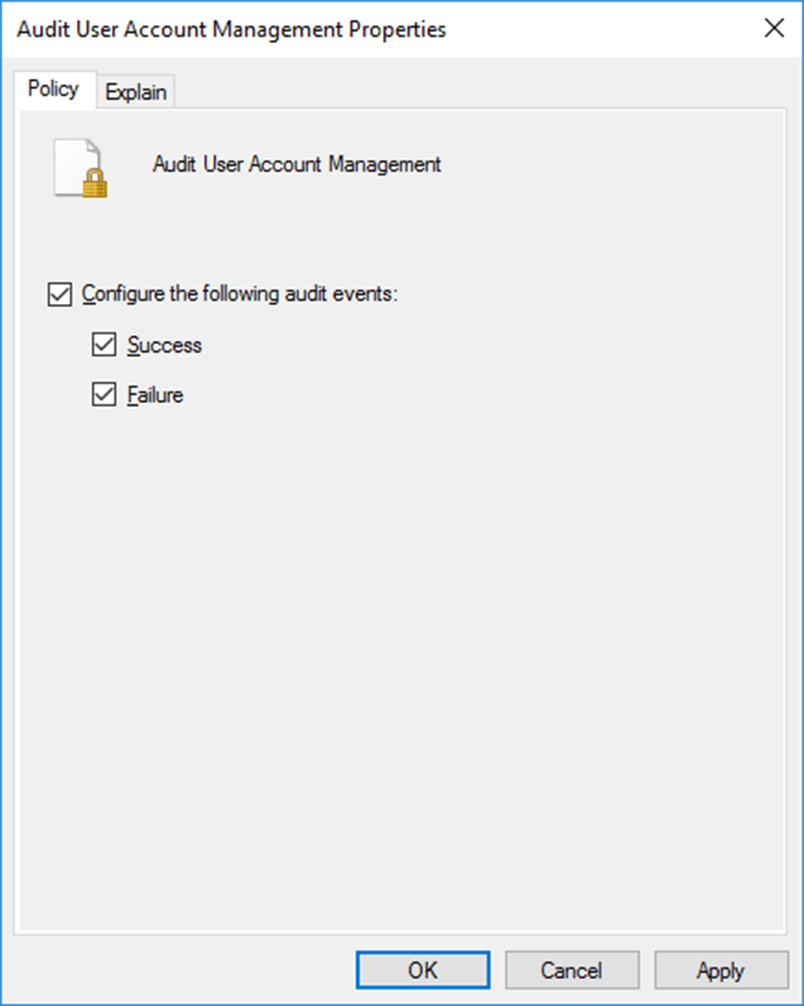
- Click Apply and then OK.
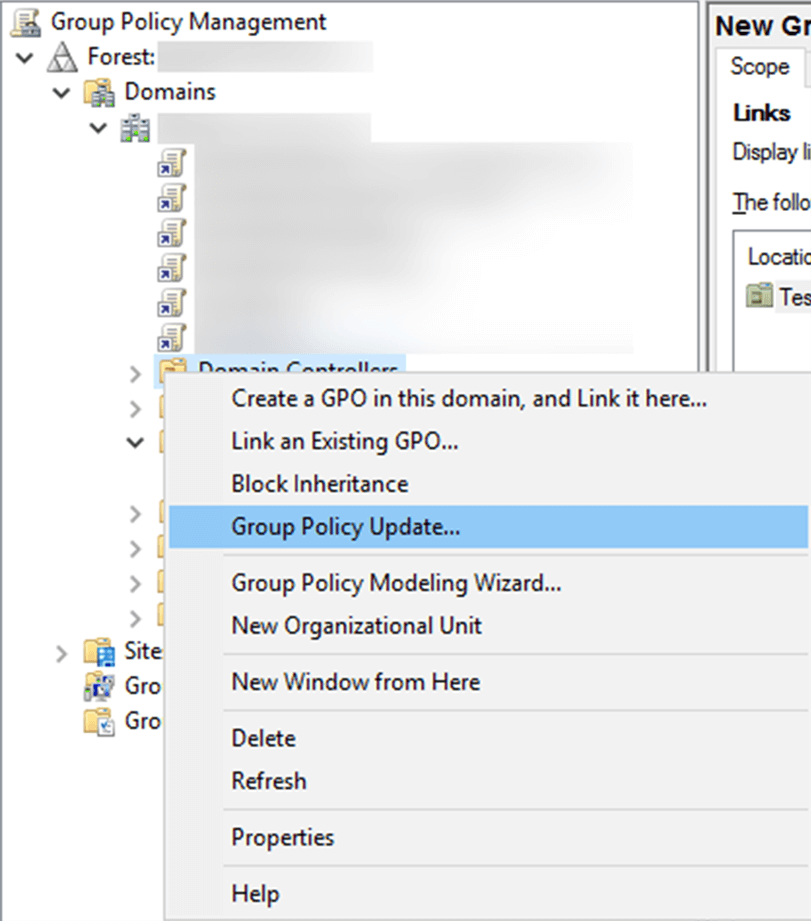
- Go back to the Group Policy Management Console. In the left pane, right-click the domain or OU that the GPO was linked to and click Group Policy Update. This step makes sure the new Group Policy settings are applied instantly instead of waiting for the next scheduled refresh.
Steps to view the logged events in the Event Viewer
Once the above steps are complete, events will be logged in the event log. These can be viewed in the Event Viewer by following the steps below:
- Open the Start menu, search for Event Viewer, and click to open it.
- In the left pane of the Event Viewer window, navigate to Windows Logs > Security. Here, you will find a list of all the security events that are logged in the system.
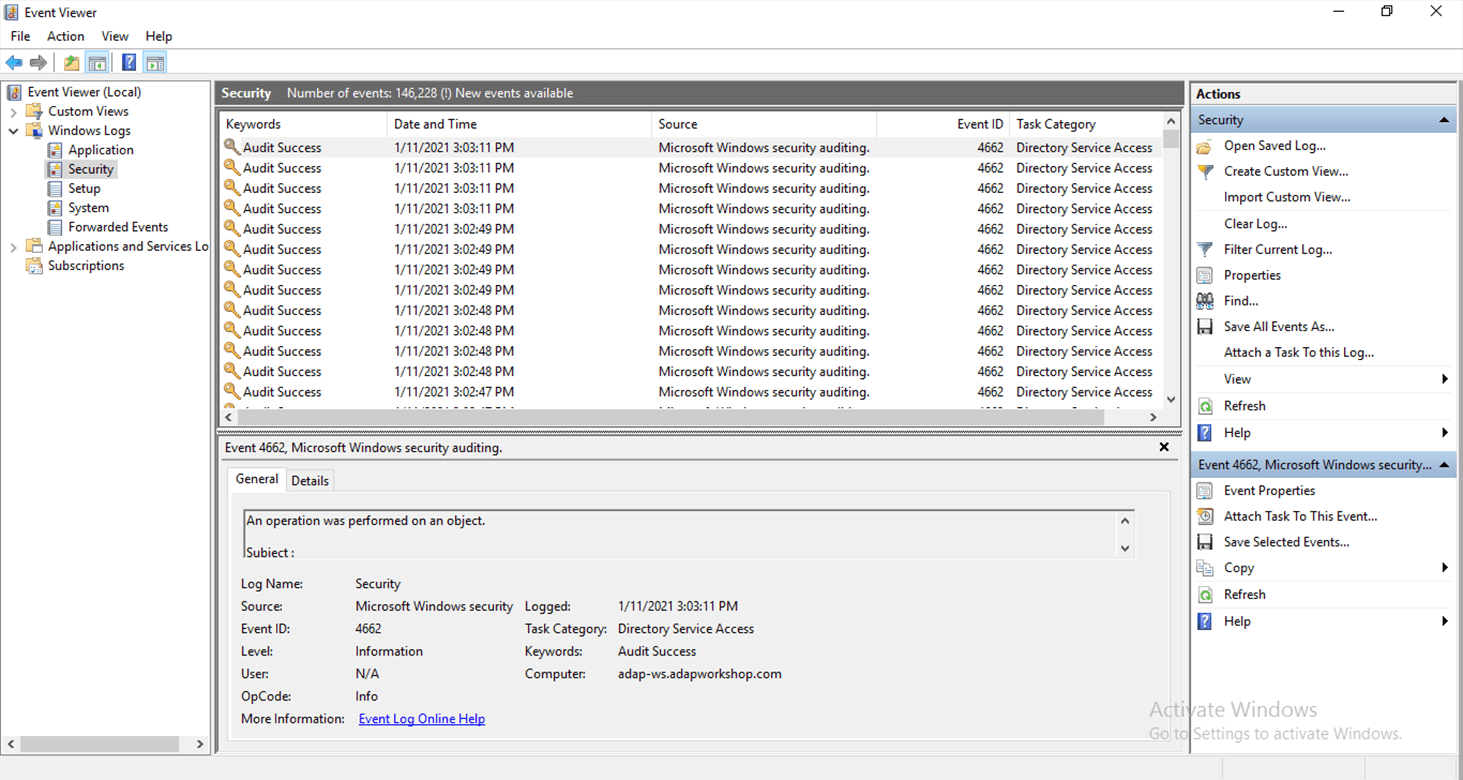
- In the right pane under Security, click Filter Current Log.
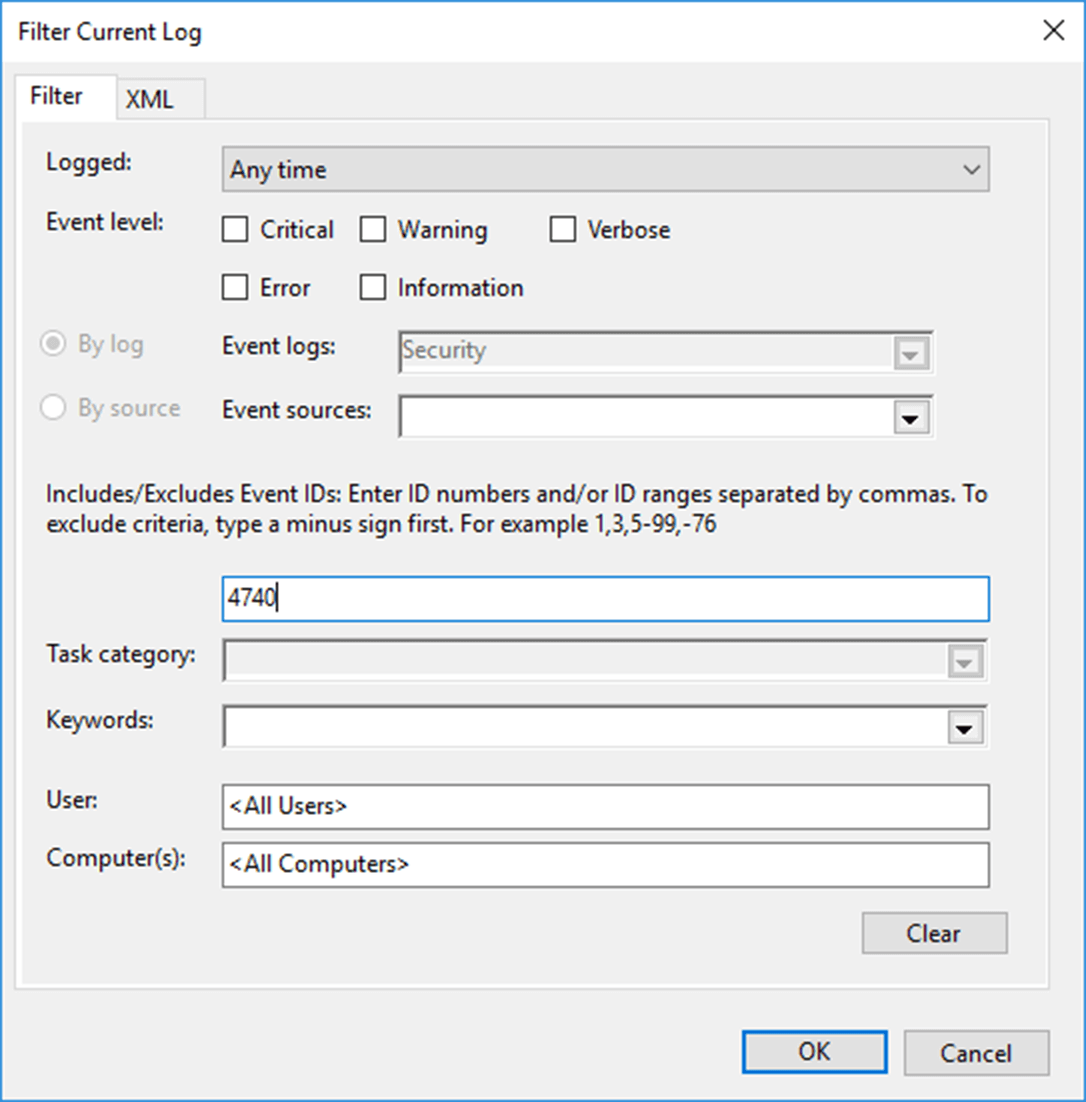
- In the pop-up window, enter 4740 in the field labeled <All Event IDs>.
- Click OK. This will provide a list of occurrences of the Event ID you entered.
- Double-click the Event ID to view its properties (description).
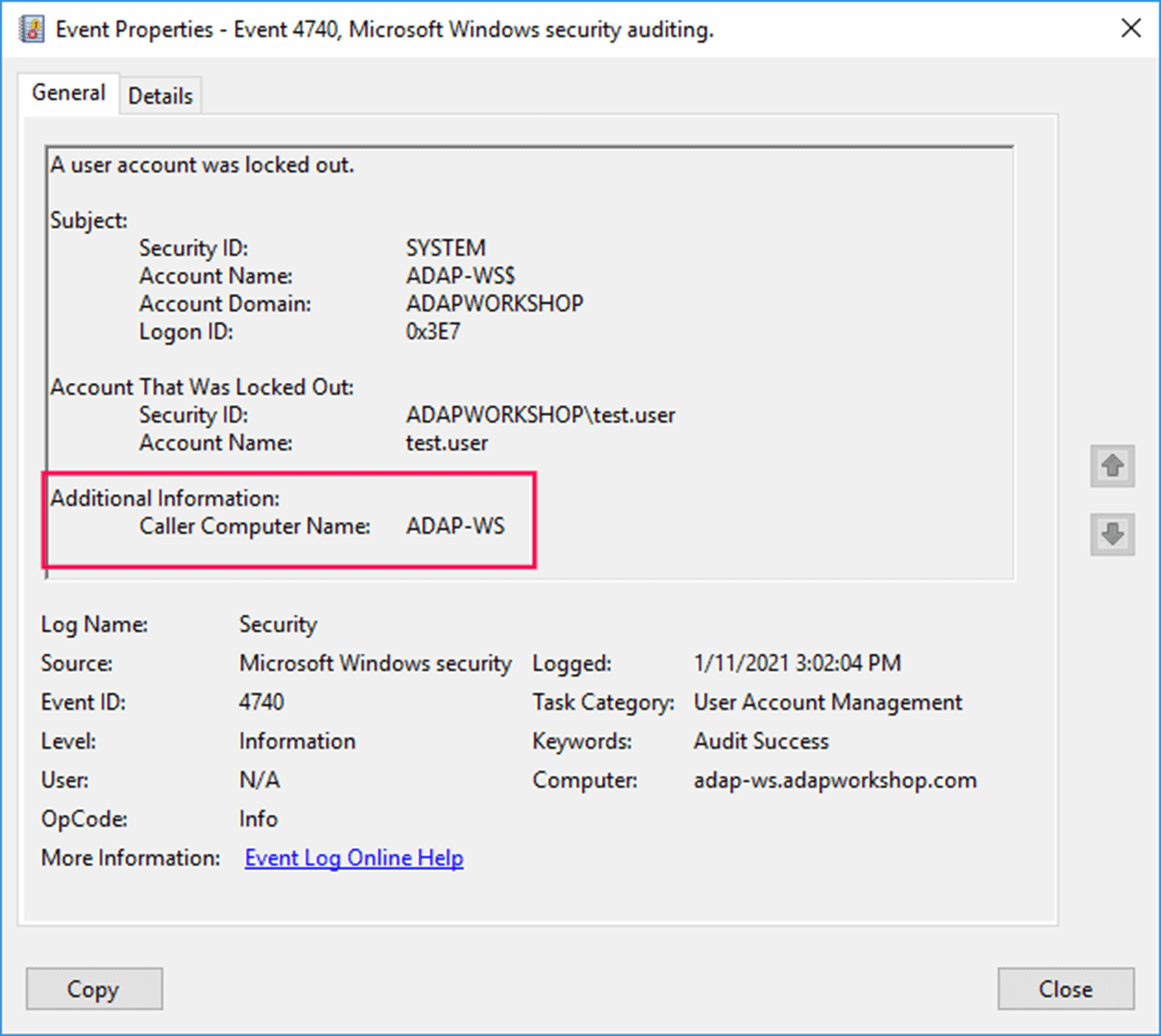
In the event description, the Caller Computer Name is shown.
To perform a more detailed analysis of the cause of this lockout, carry out the following actions on the DC:
- In the Event Viewer, filter the current view to look for the Event ID 4625, which is logged when there is a failed logon.
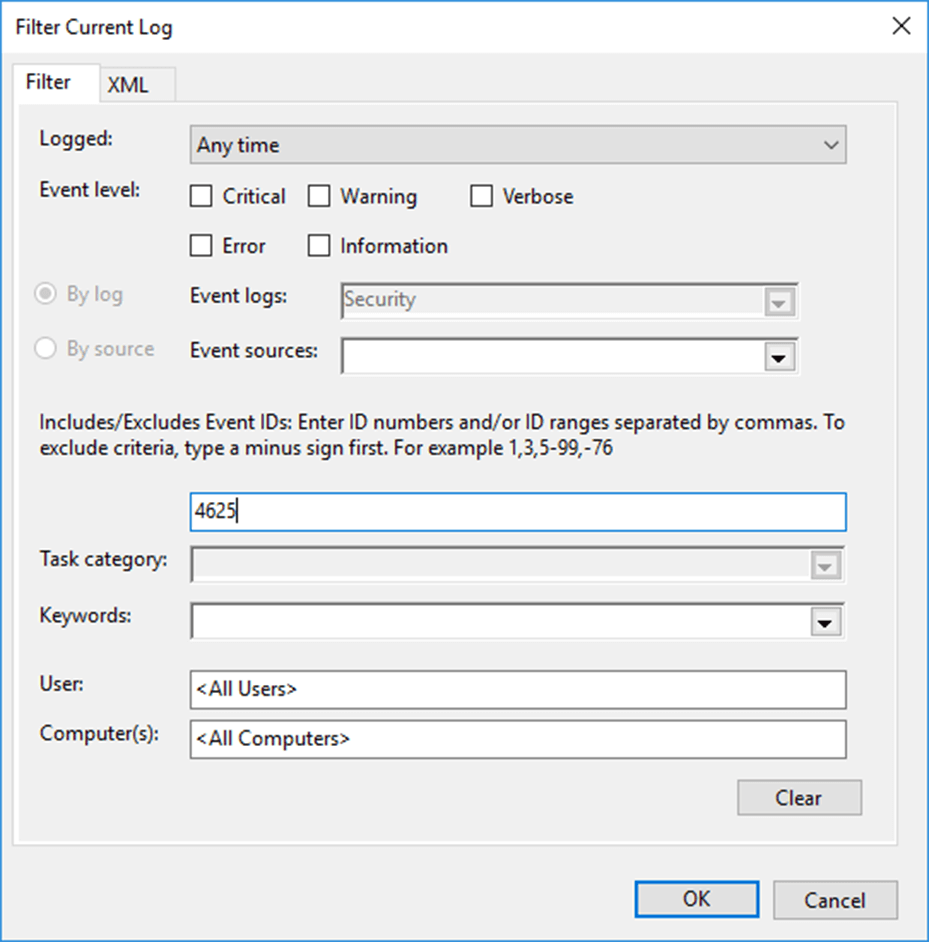
- On the right pane of the Event Viewer window, click Find, enter the name of the user that was locked out, and click Find Next.
- Look for an event that was logged after the account lockout time and view its properties.
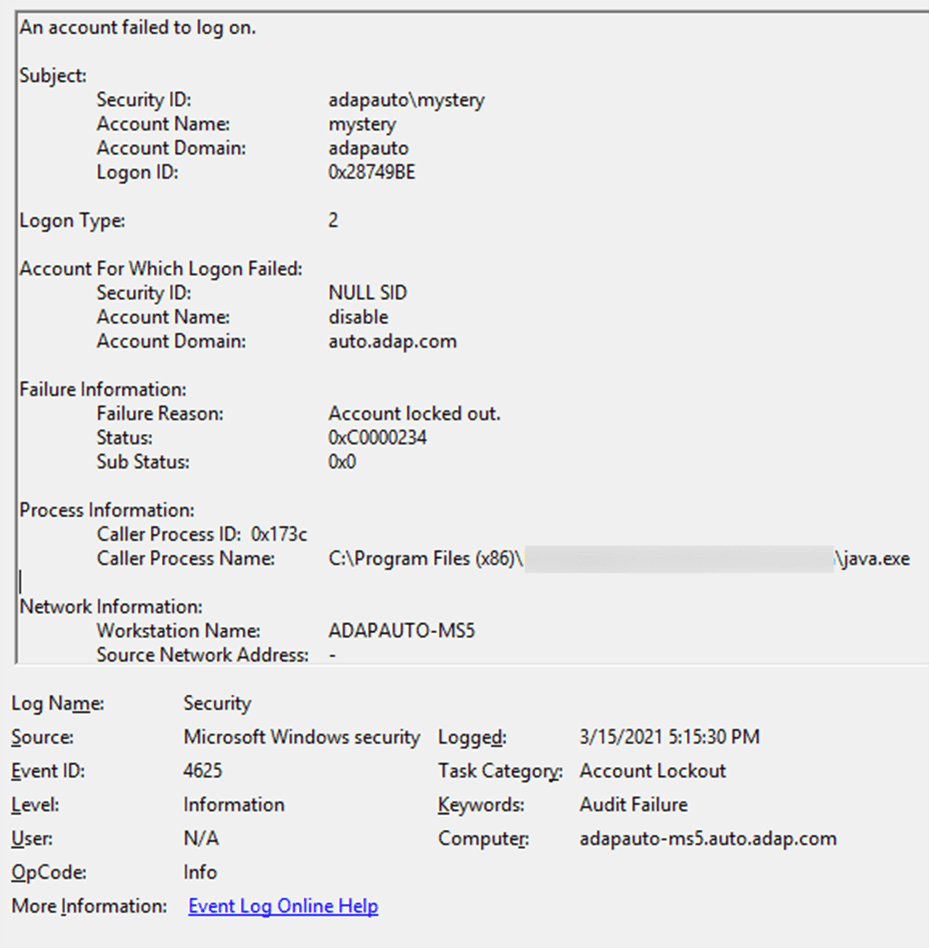
- Scroll down to Caller Process Name. This will show you the location of the process that possibly caused the lockout.
Now you need a Powershell script to check is there is locked out users and send you email alert :
powershell
# SMTP Server Configuration
$SmtpServer = "smtp.your_server_name"
$SmtpUsername = "User Name"
$SmtpPassword = "Password"
$From = "Sender_email"
$To = "recipient_email"
$Subject = "Active Directory Locked Out User Alert !"
# Get locked out users
$LockedOutUsers = Search-ADAccount -LockedOut | Select-Object Name, SamAccountName, UserPrincipalName, LockedOut
# If there are locked out users, send an email alert
if ($LockedOutUsers) {
$Body = "The following users are locked out:`n`n"
foreach ($user in $LockedOutUsers) {
$Body += "Name: $($user.Name)`n"
$Body += "Username: $($user.SamAccountName)`n"
$Body += "User Principal Name (UPN): $($user.UserPrincipalName)`n"
$Body += "Locked Out: $($user.LockedOut)`n`n"
}
# Send email
$Credential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $SmtpUsername, (ConvertTo-SecureString -String $SmtpPassword -AsPlainText -Force)
Send-MailMessage -SmtpServer $SmtpServer -From $From -To $To -Subject $Subject -Body $Body -Credential $Credential -UseSsl -Port 587
}
else {
Write-Host "No locked out users found."
}This script use smtp with SSL through port 587, you can delete the “-UseSsl” and change the port to 25 in the script in order to be more soft
And the last this is to set up Task Schedule with alert as a trigger to run this script , from event Viewer, under security, find the event ID 4740 “A user account was locked out”
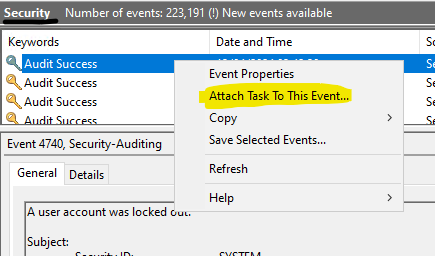
Flow the wizard to the ens and adjust the task to your need , Here you can find more information to do that :
Good luck