How To connect To console session or any other Session with Remote Desktop Connection and interact/control it
When in need to connect remotely to windows server or windows 10. You can shadow the session and just view the user session or you can control it with the user it self on the same session .
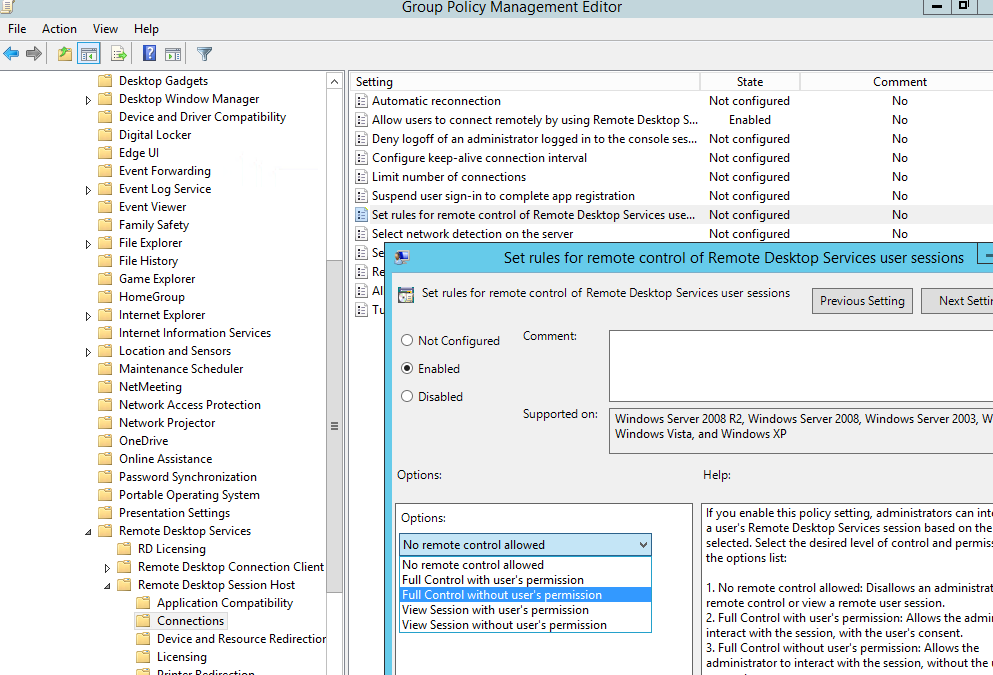
First you need to allow Remote control setting in the group policy by adding to the registry this value :
Or by adding Dword key shadow to the registry :
HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services registry key. The allowed values are: 0 – disable remote control; 1 — full control with user’s permission; 2 — full control without user’s permission; 3 — view session with user’s permission; 4 — view session without user’s permission.
You can also copy this lines-> seve it as .reg file and import it to the registry (in this case option 2)
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services] "Shadow"=dword:00000002
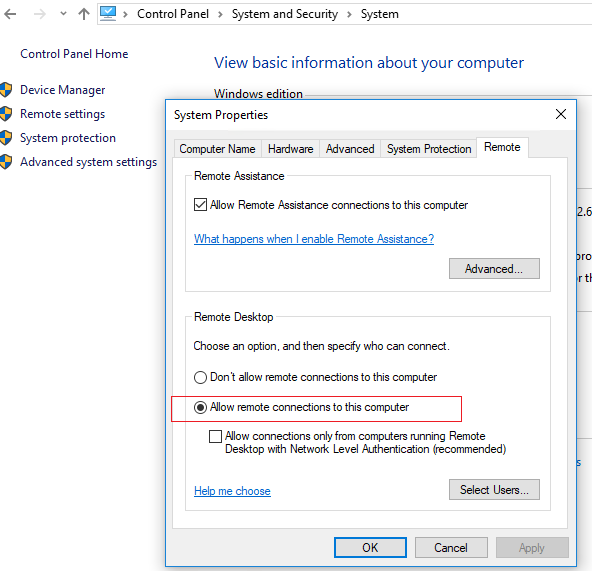
Don’t forget to enable the RDP :
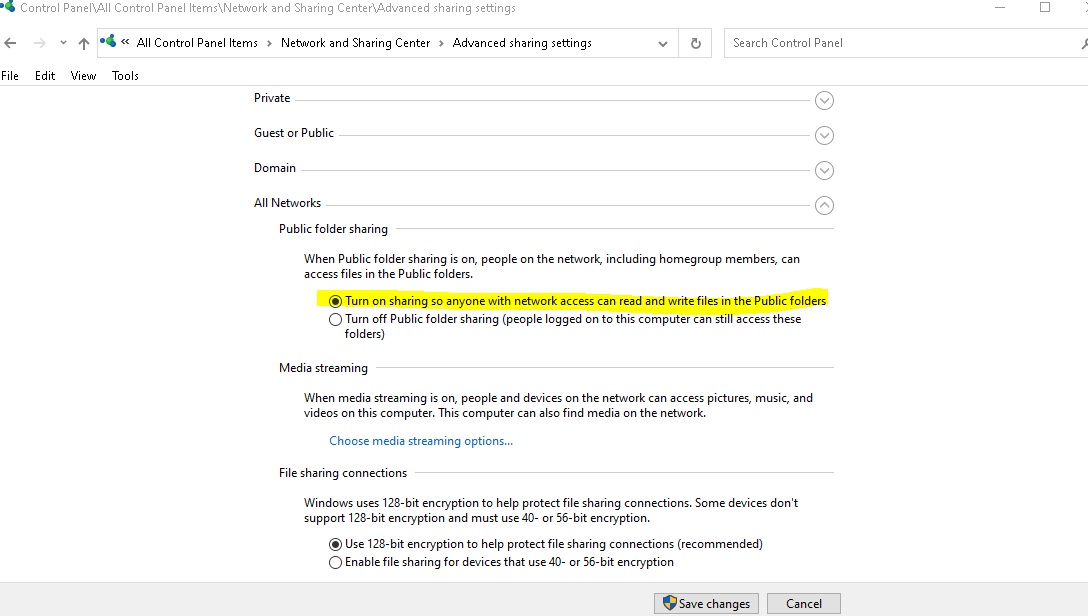
And enable network printer and sharing
Now we are ready to shadow or control the session, first you can use quser or qwinsta to get the details about the sessions on the remote computer, you can also use (with the right permissions):
query session /server:servername
now that you know the wanted session ID you can use MSTSC with all this option :
- /shadow:ID – connect to the RDP session with the specified ID.
- /v:servername – hostname or IP address of the RDP / RDS server (if not set, a current server / computer will be used).
- /prompt – request a user credentials to connect (if not specified, you will be connected with the current user credentials).
- /control – the mode that allows to interact with the user session. If the parameter is not set, you will be connected to a user session in a view mode, i. e. you won’t be able to control a user’s mouse or enter data from the keyboard;
- /noConsentPrompt – allows not to prompt the user for confirmation to connect to a session.
For example if you want just to shadow a session with out user permission or knowing, use :
Mstsc.exe /shadow:sessionID /v:Servername /noConsentPrompt
If you want to support the user and control the session the user screen
Mstsc.exe /shadow:sessionID /v:Servername /control
If you want to tkae control without the user permission :
Mstsc.exe /shadow:sessionID /v:Servername /control /noConsentPrompt
This will work also on console session aswell , command example when server IP is 192.168.1.1 and the console session id is 1, run from cmd as admin :
mstsc /v:192.168.1.5 /shadow:1 /noconsentprompt /prompt /control